Safeguard Your Facilities with BQT Electronic Safety Systems
Safeguard Your Facilities with BQT Electronic Safety Systems
Blog Article
The Future of Safety And Security: Checking Out the Newest Patterns in Electronic Safety And Security Technologies
In the world of security and security, the landscape is frequently developing, driven by technological improvements that press the limits of what is feasible. Digital security technologies have come to be increasingly sophisticated, offering cutting-edge solutions to resolve the ever-growing challenges encountered by people and organizations alike. From biometric authentication to the assimilation of fabricated knowledge and artificial intelligence, these fads hold the pledge of boosting security procedures in unmatched ways. As we browse through this intricate web of innovations, one can not assist but question just how these modern technologies will shape the future of safety and safety and security, setting the phase for a new era of defense and strength (BQT Electronic Security).
Increase of Biometric Authentication
With the increasing need for safe and secure and convenient verification approaches, the surge of biometric authentication has actually transformed the means people gain access to and protect their delicate details. Biometric authentication utilizes unique biological attributes such as finger prints, facial attributes, iris patterns, voice recognition, and even behavior traits for identity confirmation. This modern technology provides a more reputable and safe method compared to conventional passwords or PINs, as biometric data is unbelievably tough to duplicate or swipe.
Among the crucial advantages of biometric authentication is its ease. Customers no more need to keep in mind complex passwords or fret about shedding accessibility due to failed to remember credentials. By simply utilizing a component of their body for confirmation, people can swiftly and firmly gain access to their gadgets, accounts, or physical areas.
Furthermore, biometric authentication improves safety by providing a more robust protection against unauthorized access. With biometric pens being special to every individual, the threat of identification theft or unapproved entrance is considerably decreased. This heightened level of safety and security is particularly critical in fields such as financing, health care, and government where shielding sensitive details is paramount.
Assimilation of AI and Artificial Intelligence
The development of electronic protection innovations, exemplified by the increase of biometric verification, has actually led the way for advancements in the combination of AI and Artificial intelligence for improved recognition and protection mechanisms. By leveraging AI algorithms and Maker Learning versions, digital security systems can currently evaluate large amounts of data to identify patterns, abnormalities, and possible dangers in real-time. These modern technologies can adapt to advancing protection hazards and give positive actions to mitigate risks efficiently.
One significant application of AI and Artificial intelligence in digital safety is in predictive analytics, where historic data is utilized to anticipate prospective safety violations or cyber-attacks. This positive method permits security systems to expect and stop dangers prior to they happen, enhancing general precaution. Furthermore, AI-powered security systems can wisely monitor and evaluate video feeds to recognize dubious activities or people, enhancing reaction times and decreasing incorrect alarm systems.
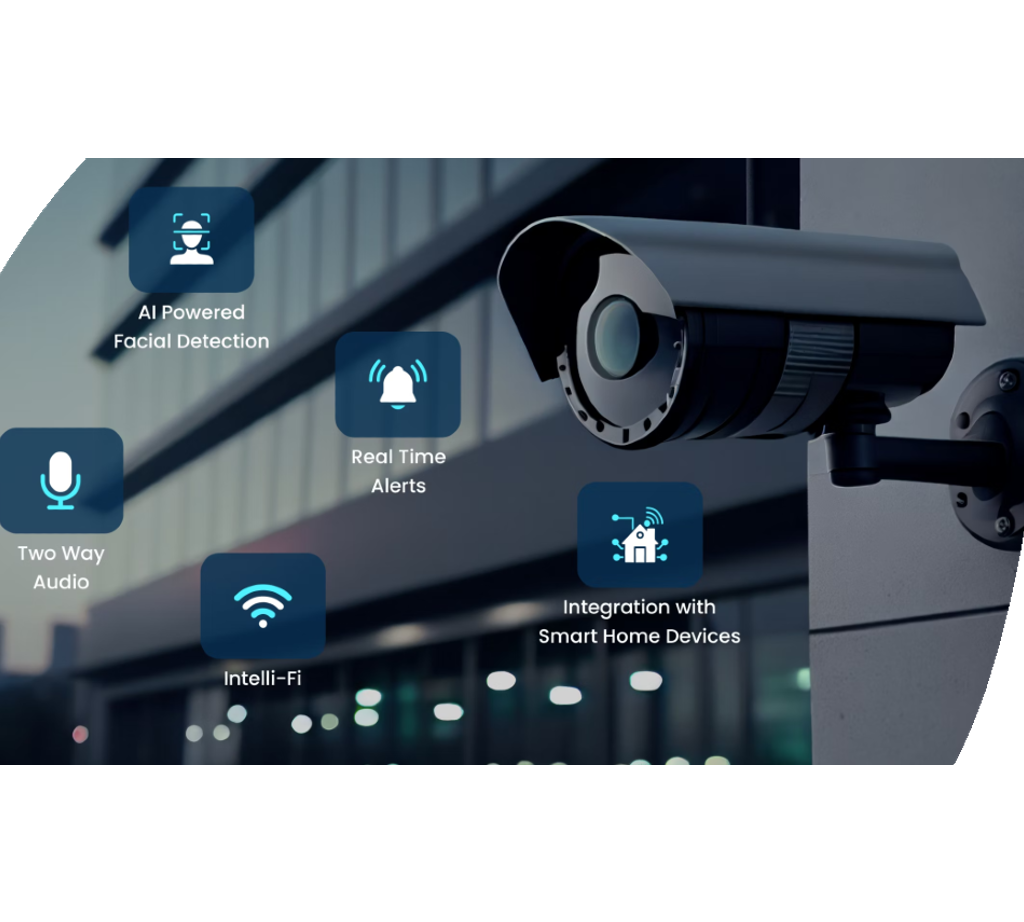
IoT and Smart Safety Tools
Innovations in electronic security modern technologies have resulted helpful resources in the emergence of IoT and Smart Safety Instruments, changing the method safety and security systems run. The Net of Things (IoT) has actually made it possible for security gadgets to be adjoined and remotely available, using improved tracking and control capacities. Smart Safety And Security Gadgets, such as wise video cameras, door locks, and motion sensors, are equipped with capabilities like real-time signals, two-way communication, and assimilation with various other wise home systems.
One of the significant advantages of IoT and Smart Security Tools is the ability to provide users with seamless access to their safety systems with smartphones or various other internet-connected devices. This comfort permits remote monitoring, arming, and disarming of protection systems from anywhere, offering house owners with comfort and adaptability. In addition, these devices commonly include innovative attributes like facial recognition, geofencing, and activity pattern acknowledgment to improve overall safety degrees.
As IoT remains to advance, the assimilation of man-made knowledge and artificial intelligence algorithms into Smart Safety and Find Out More security Instruments is expected to further boost discovery precision and modification options, making digital security systems also much more reliable and trusted.
Cloud-Based Security Solutions
Emerging as a pivotal facet of contemporary electronic security infrastructure, Cloud-Based Protection Solutions use exceptional flexibility and scalability in securing digital properties. By leveraging the power of cloud computing, these options supply businesses with sophisticated safety attributes without the requirement for considerable on-premises equipment or framework. Cloud-based security services make it possible for remote surveillance, real-time notifies, and centralized management of safety systems from any type of place with a web connection. This not only improves convenience yet also enables quick reactions to safety occurrences.
Moreover, cloud-based security services supply automatic software application updates and upkeep, ensuring that safety and security systems are always updated with the most recent defenses versus emerging hazards. In general, cloud-based safety and security services stand for a cost-effective and efficient means for services to boost their safety stance and safeguard their digital possessions.
Focus on Cybersecurity Actions
With the enhancing elegance of cyber threats, businesses are putting a critical focus on bolstering their cybersecurity actions. BQT Sideload locks. As modern technology breakthroughs, so do the techniques employed by cybercriminals to breach systems and steal delicate info. This has motivated companies to spend greatly in cybersecurity procedures to secure their data, networks, and systems from destructive strikes
Among the vital patterns in cybersecurity is the fostering of innovative file encryption protocols to guard information both at remainder and en route. Security helps to guarantee that even if information is obstructed, it continues to be unreadable and secure. In addition, the implementation of multi-factor authentication has become progressively common to include an extra layer of protection and verify the identifications of users accessing delicate info.
Final Thought

Report this page